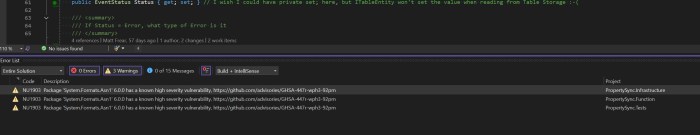
Today at a client I noticed that when I built a solution in Visual Studio, I would get Warnings about security vulnerabilities in third party NuGet packages:
We had previously setup Azure DevOp’s “Advanced Security” in our Build pipelines a while ago, so we should have already been alerted to this vulnerability, by the AdvancedSecurity-Dependency-Scanning@1 task. When I looked at the task’s output, it was rather empty:
This is because the AdvancedSecurity-Dependency-Scanning@1 task needs to have the packages already downloaded – by either doing a dotnet restore first, or a dotnet build.
The code scanning pipeline looked like this:
steps:
- task: NuGetAuthenticate@1 # needed to authenticate for our private NuGet feed
- task: AdvancedSecurity-Codeql-Init@1
inputs:
languages: "csharp"
- task: AdvancedSecurity-Dependency-Scanning@1
- task: AdvancedSecurity-Codeql-Autobuild@1
- task: AdvancedSecurity-Codeql-Analyze@1
- task: AdvancedSecurity-Publish@1
You’ll notice that I already have an “Autobuild” task there. The fix then was to move the AdvancedSecurity-Dependency-Scanning@1 to after the AdvancedSecurity-Codeql-Autobuild@1 task:
steps:
- task: NuGetAuthenticate@1 # needed to authenticate for Tcc.Common@Local NuGet feed
- task: AdvancedSecurity-Codeql-Init@1 # Initializes the CodeQL database in preparation for building.
inputs:
languages: "csharp"
- task: AdvancedSecurity-Codeql-Autobuild@1 # Build project for CodeQL analysis
- task: AdvancedSecurity-Codeql-Analyze@1 # Analyzes the code to find security vulnerabilities and coding errors.
- task: AdvancedSecurity-Dependency-Scanning@1 # scans NuGets for vulnerabilities - this needs to be after the autobuild task.
- task: AdvancedSecurity-Publish@1 # Publishes the results of the analysis to the Azure DevOps pipeline.
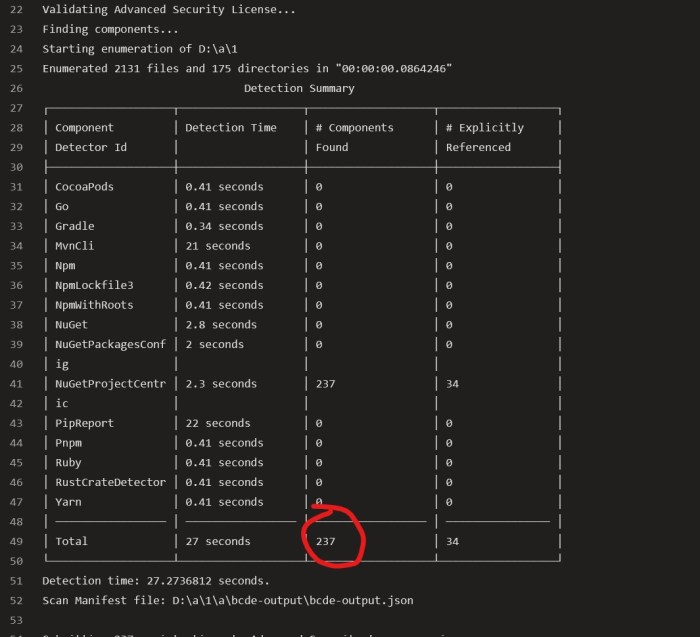
Once that was done the task detected 237 NuGet components:
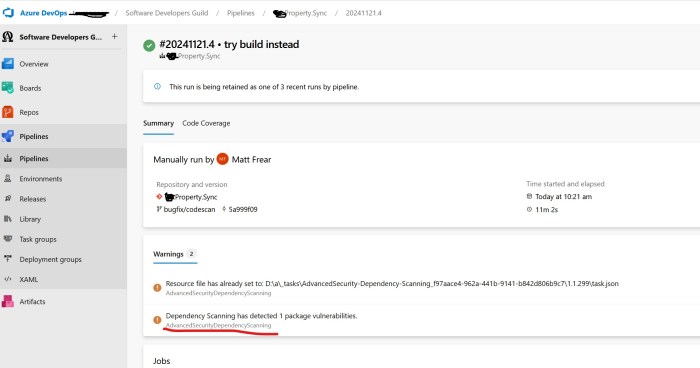
I could now see a vulnerability reported as a Build warning:
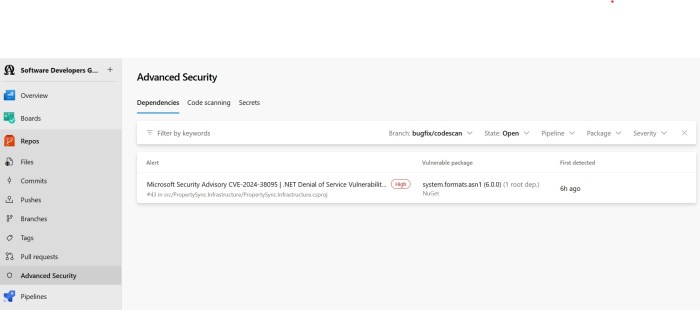
and the specific vulnerability on the Repo’s Advanced Security page: